Ransomware attacks have become increasingly common in recent years and can have profound consequences for individuals and businesses alike. Ransomware is software designed to maliciously encrypt files on a user’s computer. The attacker will typically demand payment in exchange for either decrypting the files or providing a decryption key. Ransomware and malware are sometimes used interchangeably, but ransomware is specifically a type of malware designed to extort victims into paying for restored access to their information.
A ransomware attack is particularly disruptive because it prevents all access to files on an affected system until the demands for payment are met. Even if met, files can sometimes still be damaged or corrupted because of the attack.
In this blog, we will dive into what exactly ransomware is, how it works, and how Microsoft 365 and its security features will help to protect you from ransomware and other emerging threats. Lastly, I will cover how you can quickly get started to increase your protection against ransomware.
Quantifying the cost of ransomware
The cost of ransomware varies depending on the scale and scope of the attack, but as an example of how costly the threat can be, in 2022, the average cost of a data breach in the United States was $9.44 million. In total, the cost of those attacks was over $20 billion (about $62 per person in the US) in 2021. By 2031, estimates are that this number will be closer to $265 billion. With the risk and cost associated with ransomware, it is easy to see the importance of protecting yourself from the threat.
What ransomware is and how it works
Any ransomware attack begins with an initial point of compromise. From this initial point of compromise, code is executed that encrypts files on the impacted system. A message is usually presented to the user of the affected system describing the encryption and making a demand for payment.

Often, a phishing email is used to gain access to the initial point of compromise. Phishing emails are messages from malicious senders that appear legitimate communication, usually from a known source. These messages intend to fool the recipient into clicking on a link within the message or opening an attachment. When the recipient clicks the link or opens the attachment, malicious code is executed that begins the encryption process.
Once your files have been encrypted by ransomware, there is no guarantee paying the ransom demanded will restore access to your files. In fact, the FBI recommends against paying a ransom in response to an attack for this reason. If you are a victim of ransomware, you should instead contact your local FBI field office to request assistance, or you can submit a request for assistance online.
How Microsoft 365 and its security features help protect from ransomware and other emerging threats
Microsoft 365 uses various security features and services to protect against common malware, ransomware, and virus threats.
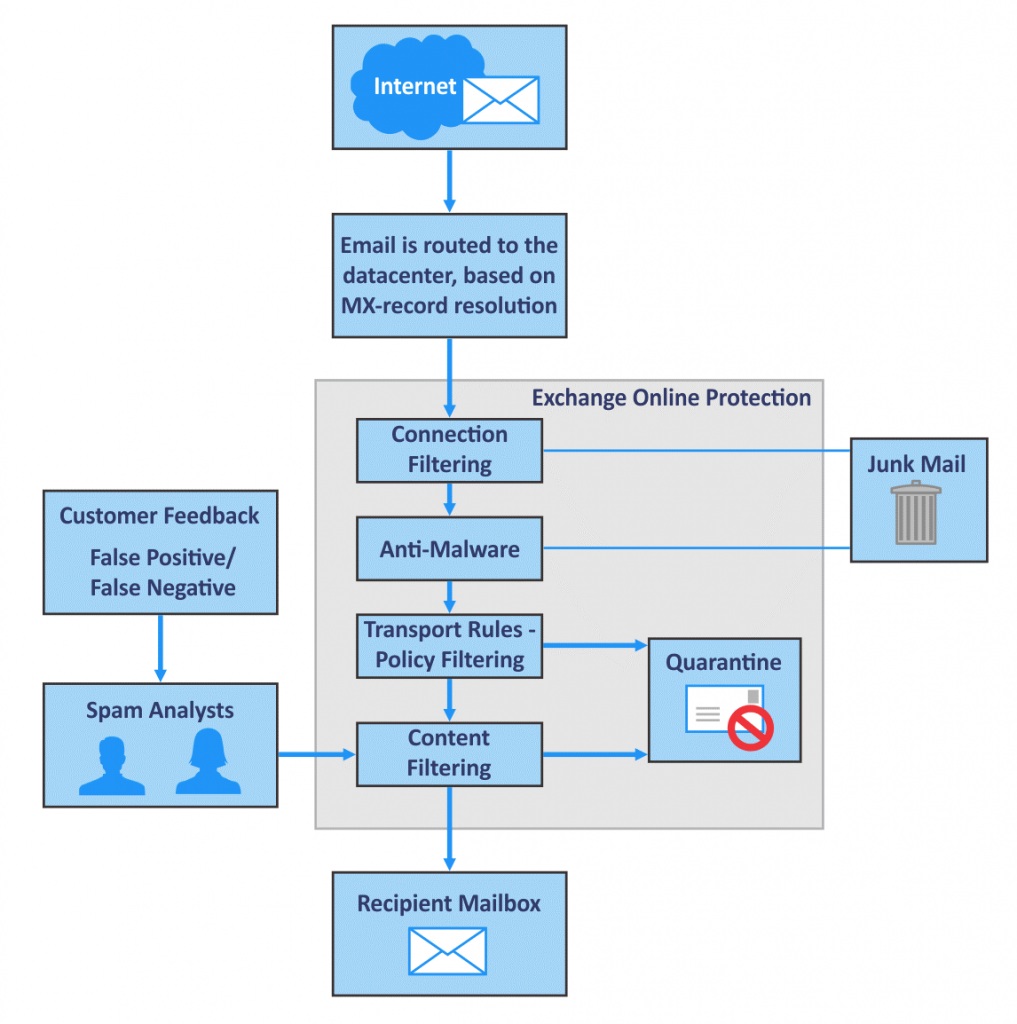
Exchange Online Protection
All organizations that use Microsoft 365 and Exchange Online will have mail routed through Exchange Online Protection (EOP). EOP is a multilayered malware protection service that uses multiple anti-malware scan engines to check all messages as they come in and go out of your organization.
Messages flagged as containing malware are quarantined according to your organizational quarantine settings. At the service level, Microsoft monitors threats detected by EOP across all their Microsoft 365 tenants. This central monitoring allows Microsoft to respond to new threats by creating policy rules that centrally detect and quarantine the threat. These rules are then published to the Microsoft global network regularly (currently every two hours).
Office 365 Advanced Threat Protection
Office 365 Advanced Threat Protection (ATP) is a feature of Microsoft Defender for Office 365 that protects your organization from malware, phishing, and virus threats by providing cloud-based filtering of messages, scanning for unsafe attachments, links, or other factors that might indicate a message has nefarious intent. It includes the Safe Links and Safe Attachments functionality and your organizational anti-phishing and anti-malware policies.
Safe Links
The Safe Links feature scans URLs in messages and Office documents and blocks URLs with malicious payloads. These scans happen every time a user clicks on a link, and malicious links are blocked dynamically. Because links are scanned on every attempt to access, even a “good” URL that is later modified to deliver malware would be flagged, and access blocked.
Safe Attachments
As previously discussed, all email attachments coming into and leaving your organization are scanned by EOP for malware as a part of EOPs (Exchange Online Protection) standard malware protection. The Safe Attachments feature provides an additional layer of malware protection by performing a secondary scan on email attachments.
With the Safe Attachments feature enabled, a secure sandbox is created, and attachments are examined within that secure sandbox for any indications of abnormal behavior or indicators of malware. If any indicators are detected, the attachment is removed according to the setting you provided in your organization’s Safe Attachments policy.
Zero-hour Auto Purge (ZAP)
Sometimes, users can receive a message containing an attachment or URL that does not appear malicious on receipt. The content can later be weaponized by changing the payload at a URL, activating code within an attachment, or changing what an attachment does when opened.
Microsoft continually monitors for updated spam and malware signatures. As new signatures are added to the service, messages already delivered to users are checked against these updated signatures. Suppose, for any reason, any already delivered message is found to be later classified as malware or phishing message. In that case, Zero-hour Auto Purge will seamlessly remove these messages from the users inbox and move them to either junk or quarantine based on your organizational policy settings.
Simulated Phishing Attacks
Organizations with an M365 E5 or Microsoft Defender for Office 365 Plan 2 license gain the capability of running realistic simulated phishing attack scenarios using a feature called attack simulation training. Attack simulation training gives you the ability to run a variety of simulated attacks, including credential harvesting, malware as an attachment, malware as a link, and hybrid credential harvest attacks.
You decide the type of attack simulation to run and the users you want to target with the simulation. Details of how your users respond to the simulated attack are reported in Defender for Office 365. You can use these behavioral insights to provide additional user training or remedial guidance for users who need it.
Preset Security Policies
While administrators can customize their M365 security settings, Microsoft provides their best practice configuration guidance for EOP and Defender for Office 365 policy settings by providing two preset security policy level settings – standard and strict.
Choosing between one of these two pre-set policy security levels according to your organizational security posture will provide you with best practice values for critical policy settings.
The specific policy settings associated with each of the two pre-set security levels are available for review so that you can see the settings and values that are being adjusted.
Additional Security Considerations
While not specific to ransomware threats, there are other security measures you should consider taking to improve the overall security posture of your organization and better protect your digital assets.
Multi-factor Authentication
Consider requiring users who access your Microsoft 365 services or organizational data to use two-factor or multi-factor authentication (MFA). Requiring MFA provides extra security at user sign-in by requiring that the user provide an additional verification method beyond just their password. MFA occurs after initial sign-in and is usually based on something the user has with them, like a registered smartphone device or biometric authentication using fingerprints, face scanning, or other biometric markers.
Because MFA occurs after the user supplies their username and password, even with a compromised password, an attacker would still need access to the second authentication method before they can access services.
Conditional Access Rules
Conditional access policies let you define exact criteria for who can gain access to your organization’s content and services, as well as how they can connect and consume these services.
You can use signals like the type of device the user is attempting to connect with, the location they are connecting from, the application they are trying to access, and a variety of other signals that let you granularly define your requirements.
Organizational data used to reside within the company network, protected by a firewall from the general internet. As company information moves to cloud services, it is imperative to modernize your security to protect this new reality. Conditional access policies help you do that so you can provide this “anywhere” access while also providing the necessary security for your data.
How to Recover
Despite efforts to prevent them, ransomware attacks can and do happen. If you find that you are a victim of a ransomware attack, there are some basic steps that you can take to help prevent the damage and get back to productivity as quickly as possible.
Go Offline
Once you are aware that a system is infected with malware, it is best to disconnect the device from your network and any other external storage. The idea is to isolate the impacted systems and limit the spread of the malware as much as possible.
Monitor Activity
Once you have identified the impacted systems within your organization, the next step is to review logs and other heuristic data to see if there has been any usual activity on your network or other unaffected systems.
Try to Identify the Ransomware Being Used
Investigate impacted systems and determine the type of ransomware used in the attack. If you can successfully identify the type of ransomware, security researchers may be able to provide a decryption/decryptor tool.
Recover or Rebuild Impacted Systems from Backup
Be prepared in advance for the possibility of a ransomware attack by regularly backing up critical systems and organizational data. Keep these backups stored in a location disconnected from your corporate network so they cannot be impacted by ransomware attacking systems on that network.
Where to go from here?
Ransomware is a real and challenging threat to protect against. Microsoft 365 offers a set of powerful tools to help you combat this threat and protect your data.
Understanding how these tools work together to provide best-in-class cloud security and guiding customers in implementing those tools within their organization is one of the areas that we specialize in here at Olive + Goose.
If you are interested in learning more about any of the topics discussed in this post or find that your organization needs assistance in understanding or implementing any aspect of Microsoft 365 security, please contact us at [email protected].
Featured image: “Image by Kerfin 7 on Freepik “Free Photo | System background compromised by hacking 3d illustration (freepik.com)
